How to Control Your Access Points with a Workplace Sign In System

"Have you seen the delivery person? I was expecting a shipment 15 minutes ago.”
“Oh, I think he arrived. Check the copy room.”
As common as this conversation sounds, a scenario like this actually reflects some of the modern security issues businesses face today.
Access points refer to the points in and out of your business, and controlling them effectively is more important than ever in order to protect your employees, visitors, and assets. This can be a challenging task if you haven’t taken the time to evaluate your existing security procedures to close the gap on any weak points.
If you think your employees aren’t concerned—think again. Research shows that many employees are feeling anxious about their health and safety in the workplace, especially as businesses strategize to reopen during the pandemic. If you haven’t already started, you should seriously think about implementing solutions to protect them.
Did you know that workplace safety and security can be improved significantly with the help of a digital sign in system? In this article, we’ll look at why you should consider it if you’re not already using one and how to maximize it for access control if you are.
Why use a Sign In. System for Access Control?
A sign in system lets you control access points by monitoring what we call our four security ‘W’s’:
- Who is entering your premises
- What is the purpose of their visit
- When will they be arriving, and leaving
- Where do they require access
For those businesses that share a building with other organizations, controlling access points is even more important. Using separate systems for access control and visitor management can lead to:
- Segmented reporting, which can make it difficult to use data for actionable insights
- Inefficient processes, in the form of different employees doing the same task but using independent systems
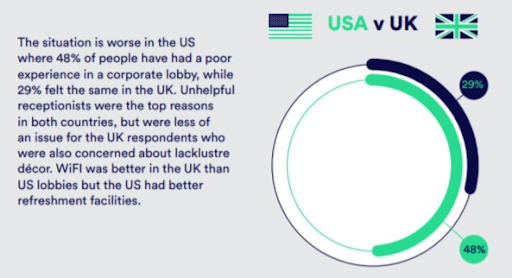
- Poor lobby interactions for visitors, which a 2018 survey found impacts about 48% of corporate lobby visits and results in negative impressions a company
Compare these negatives with the positives that integrated systems can bring, and you can see why a comprehensive workplace sign in system like SwipedOn makes sense:
- Staff benefit from precise operational procedures for entering the premises and admitting guests.
- Visitors enjoy a streamlined, contactless sign in process.
- Managers get improved security and facilities utilization insights from comprehensive reporting.
- Companies see improvements in multi-site management and integration.
- Locations maintain better compliance with government regulations, like being able to include mandated QR codes for COVID-19 contact tracing.
So, we’ve covered the benefits of integrated access control and sign in systems, let’s look at how you might go about implementing it at your office.
How to Integrate Access Point Control with your VMS
Integrating sign in systems with access point control is a multi-step process. This can make it seem like an intimidating task to tackle but don’t let that put you off. Given that 86% of respondents to this 2020 survey saw visitor management as “very important,” it isn’t something that should be disregarded.
Here’s an overview of the steps you can take to integrate access point control with a VMS.

1. Align Visitor Management and Security Goals
To create a visitor management strategy that meets your organization's needs, start by considering the scope of potential threats:
- Do you need to reduce theft?
- Are there any hazardous locations in your office that pose a risk to unattended personnel?
- Do you have areas of high mixed staff and visitor traffic that require more involved management practices?
As a proactive solution to these potential needs, plan out how you can address them using existing security systems, policies, and personnel. Also, consider what new visitor management resources (such as a digital sign in solution) your organization may need.
2. Collect Visitor Sign in Information
Collecting visitor information is important because it helps identify who you’re admitting and why. Who enters your premises can vary greatly and admittance should be based on the security goals you’ve set.
When collecting sign in information, consider whether you need to record:
- Visitor name and contact information
- Who to contact in case of an emergency
- Temperature readings and other health information
- Department or employee being visited
- Sign in time and date
- Expected length of visit
- Who is the staff member responsible for the visitor

3. Create an Evacuation Plan for Visitors and Employees
Helping visitors and employees safely evacuate the premises in the event of an emergency is also a key concern. Therefore, integrating access point control using a VMS also involves addressing how to evacuate visitors.
Your evacuation plan should include provisions for:
- Contract workers and other facility personnel who are not on employee lists and directories, but enter the premises regularly
- Delivery people, service technicians, and other individuals servicing specific areas as-needed basis
- Occasional but specific guests with limited access to your facilities (e.g., VIPs, staff family members, customers/clients
You should also make sure that employees are familiar with the evacuation plan and their role in ensuring visitors also know how to safely exit the premises, consider including mock visitors in your evacuation drills.
A good sign in system helps to conduct employee roll calls as well as helping first responders determine the whereabouts of visitors to evacuate them through controlled access points.
4. Merge Workplace Sign In Into Existing Security Systems
Integrated sign in systems can be a driving force for good when it comes to both security and making visitors feel welcomed.
Integrating visitor management and sign in with your access control system clears the way for streamlined, secure entry of visitors at critical checkpoints. Ensure visitors only have access to designated areas while making sure restricted locations are not accessed.
You can integrate your existing security imaging systems to efficiently handle deliveries by scanning a package’s barcode. Then, for example, opt to notify the recipient of the arrival of a package or, use your sign in system to guide the delivery person to a designated drop-off point.
5. Centralize User Management
Centralizing access control to a comprehensive but easy to use system saves time and effort. It reduces the chance of errors and allows administrators to monitor activity across multiple systems more effectively.
With centralized user management, there’s no need to worry about registering visitors into different components of a security system. This reduces the chance of errors slowing down performance and makes generating comprehensive reports easier. It also allows IT to maintain a single database for all visitor and access control management tasks.
6. Analyze Visitor Data
A visitor management system is an essential tool for complying with regulatory standards. You can use the data collected by your VMS to get a better understanding of security and business processes in your organization, which will lead to more effective policies over time.
Data analysis might reveal questionable patterns that staff were not aware of. For example, denied access attempts in the same location could indicate an incorrectly trained employee or a potential insider threat trying to access a secure area. Gathering this data can help companies make risk-informed decisions to improve their operations.

7. Review and Optimize Your Systems
The security risks to any business are constantly changing, by regularly evaluating the performance of your visitor management system you can help to eliminate outdated practices and find new opportunities to protect your business, employees, and visitors.
Access point control has evolved from being focused primarily on security to being a crucial component for maintaining the health and well-being of the workforce due to the COVID pandemic.



-929560-edited-003563-edited.jpg)





 Germany - Deutsch
Germany - Deutsch